Advantages of Message Authentication Code
Like any of the MAC it is used for both data integrity and authentication. This new authentication system is based on the OWIN Open Web Interface for NET.
The code is unusable to everyone.

. Mobile Device Two-Factor Authentication. RabbitMQ Message Queue Using NET Core 6 Web API. Without challenge-response authentication it would be impossible to perform activities like online banking with a high degree of security confidence.
Below are the download links. JSON Web Token JWT Grant is an OAuth 20 flow that is used to grant an access token to service integrations. This is the oldest and the most well-developed method of biometric authenticationIt is also the most commonly used typeFingerprints can be collected using optical or thermal techniques.
The following are the advantages of Windows Authentication. A service integration integrates directly with a DocuSign account and does not. Authorization Code Grant authentication.
RFC 2865 RADIUS June 2000 The Access-Request is submitted to the RADIUS server via the network. The major disadvantage to using Basic authentication over non-encrypted means of communication is that the clients user name and password are sent as a base-64-encoded plaintext message making it very easy for a malicious user to eavesdrop on the communication and retrieve the user name and password. Knowledge something only the user knows possession.
In the Authorization Code Grant flow your client integration obtains consent from an individual to perform actions on their behalf then receives an authorization code that can be exchanged for an access token which is required to. Service integrations differ from user integrations which authenticate through the Authorization Code and Implicit grant flows in that. JSON Web Token JWT Grant authentication.
For example gaining access to an online account by entering a code sent as a one-time password using a fingerprint to unlock a mobile phone and accessing a website through a Facebook login are all common examples. Authentication also enables accountability by making it possible to link access and actions to specific identities. The ticket will be in encrypted form.
The resulting print is enhanced and processed with sophisticated algorithms to build a digital biometric template. Encompassing authentication or 2FA along with similar terms is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence or factors to an authentication mechanism. The user will decrypt the message and get the hash code.
In the domain of network encryption this technique is known as symmetric encryption. We will show a message box to guide you to install the 64-bit version on Windows. Sure its old school but youll appreciate it if you.
The header element can be used to contain information such as authentication information or the definition of complex data types. The envelope element is the mandatory element in the SOAP message and is used to encapsulate all of the data in the SOAP message. We currently use a line based representation of the text buffer which has some serious advantages but also disadvantages especially in terms of memory consumption for example a file with very many short lines.
Application with a Button and a List box control to access all files that reside in the temp folder as in the following code. Checking data integrity is necessary for the parties involved. Protected void btnAccessFiles_Clickobject sender EventArgs e.
Most people have used token-based process in some form. Validating this identity establishes a trust relationship for further interactions. ASPNET Core Identity is basically a membership system that provides login functionality including user registration in any ASPNET Core applications.
This new authentication system is intended to replace the existing membership system of classic ASPNET. Behind the scenes Swoops technology conducts three layers of security measures to determine if the email came from the correct user. Each method has its own advantages and disadvantages.
The user sends a message to KDC requesting keys so that the user can prove its authenticity and access the services of the Network. Its used to authorise information filed online and is the equivalent of a. Many services can also provide a special code that you can print out and save in a safe place.
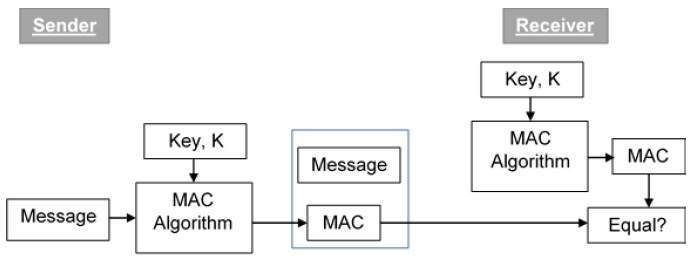
Keep your authentication code safe The authentication code is a 6 digit alphanumeric code we issue to each company. HMAC Hash-based Message Authentication Code is a type of a message authentication code MAC that is acquired by executing a cryptographic hash function on the data that is to be authenticated and a secret shared key. Authentication means verifying the identity of a user device or other entity who wants to use data resources or applications.
That way they can focus on maintaining a strong and. If no response is returned within a length of time the request is re-sent a number of times. The hash code is again sent back to AS.
Many two-factor authentication systems can supply an authentication code via a voice message. Here challenge-response authentication is the only thing preventing a criminal from accessing the sensitive files credentials and information stored in a computer system. Now AS Authentication server in KDC will send the ticket back to the User.
The client can also forward requests to an alternate server or servers in the event that the primary server is down or unreachable. Each SOAP message consists of an envelope element a header and a body element. By implementing an authentication method like this users will only have to manage the password for their email address and not have to handle a new one for your website.
Authorization Code Grant is an OAuth 20 flow used by server-hosted integrations to obtain an access token. There is a need to secure the unique key in such processes as the system or person familiar with the key has full authentication to decrypt the message for reading. All authentication tokens provide users with access to a device or.

Dr Alejandra Flores Mosri Message Authentication Internet Management Security 06 Learning Outcomes At The End Of This Session You Should Be Able To Ppt Download

Dr Alejandra Flores Mosri Message Authentication Internet Management Security 06 Learning Outcomes At The End Of This Session You Should Be Able To Ppt Download

Security Analysis Of Sms As A Second Factor Of Authentication December 2020 Communications Of The Acm

Dr Alejandra Flores Mosri Message Authentication Internet Management Security 06 Learning Outcomes At The End Of This Session You Should Be Able To Ppt Download
Comments
Post a Comment